What is Yokogawa’s lifecycle approach for cybersecurity?
Yokogawa’s cybersecurity services take a lifecycle approach to help customers control the security risks and manage to achieve the highest business continuity plan throughout the plant’s entire lifecycle. We focus on long-term lifecycle services while understanding customers' challenges and working continuously for improvements in a close partnership. Yokogawa follows one overall objective: to minimize risk and maximize corporate values according to our self-commitment as a lifecycle value partner. We aim to become your #1 trusted partner and achieve long-term, stable, and secure operations.
Implementing a Security Program
Taking a lifecycle perspective, Yokogawa’s Security Program delivers resilient cybersecurity services and solutions to reduce cyber risks in customer’s ICS environment. The program combines over 100 years of expertise in industrial automation, best practices in cybersecurity architecture design, and plant operations knowledge to ensure safe and secure operations, which is the paramount priority for our customers and Yokogawa.
-
Cybersecurity Awareness & Training
Despite the best cyber defenses, human error leads to many cyber incidents, due to a lack of cybersecurity knowledge and awareness.
Details
Table of Contents
Customers Challenges
A recent FM Global Survey of 200 business leaders at Fortune 500-size organizations found 84% of them categorize a cyber-attack on industrial control systems as a “major concern” for their business. Read FM Global survey
Since over a decade ago, cybersecurity has become a significant factor in the overall risk management cycle for industrial installations, process plants, and other critical assets (i.e. sensors, motors, and other control devices). Among our customers, there is a wide understanding of the potential benefits of the IIoT (Industrial Internet of Things), Cloud, and Industry 4.0 transforming operations bringing industry innovations, better products, smarter services, and higher work efficiency. At the same time, posing cybersecurity risks for safety and business continuity has challenged customers to open a new digitalized world securely.

Our solutions: Industrial Applications of Cybersecurity Lifecycle Management
Yokogawa always supports our customers to achieve the Cybersecurity Lifecycle Management at the heart of Sustainable Growth Strategy.
Yokogawa considers that both IT and OT have converged in today's industrial control system environments and there is an even greater need for a common understanding between all those who support or rely on these systems.
Hence, Yokogawa delivers a complete industrial security program across customers’ entire organization, from the corporate level to plant sites.
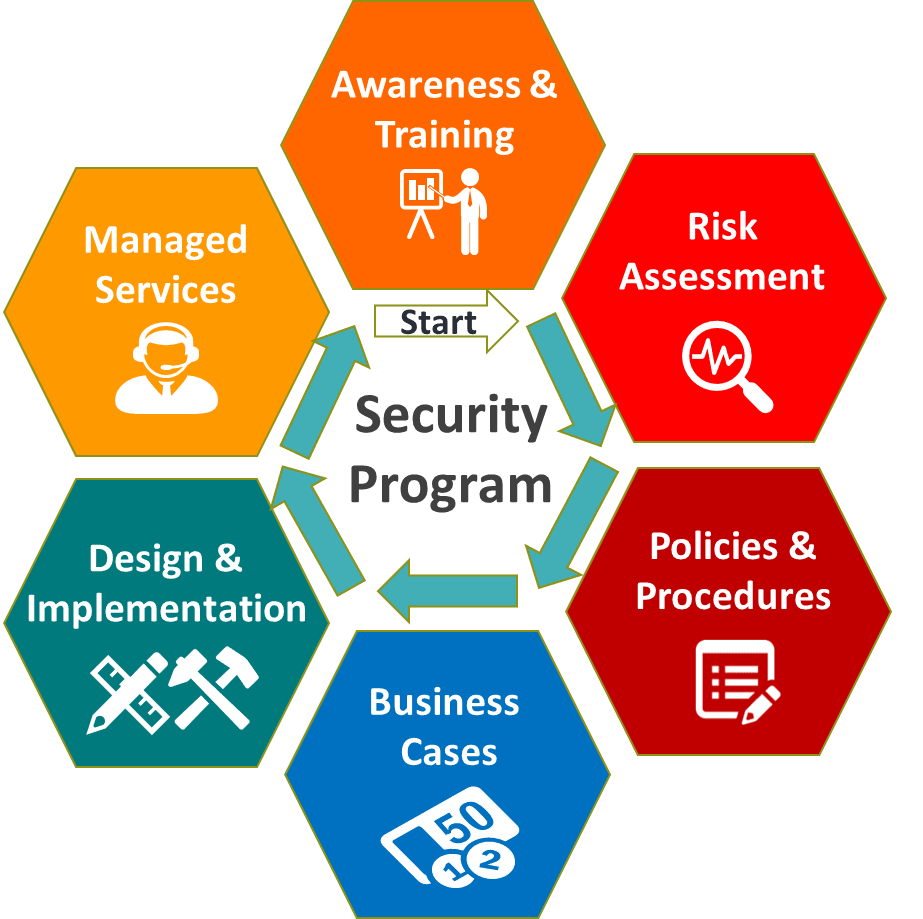
Delivering Services in Security program
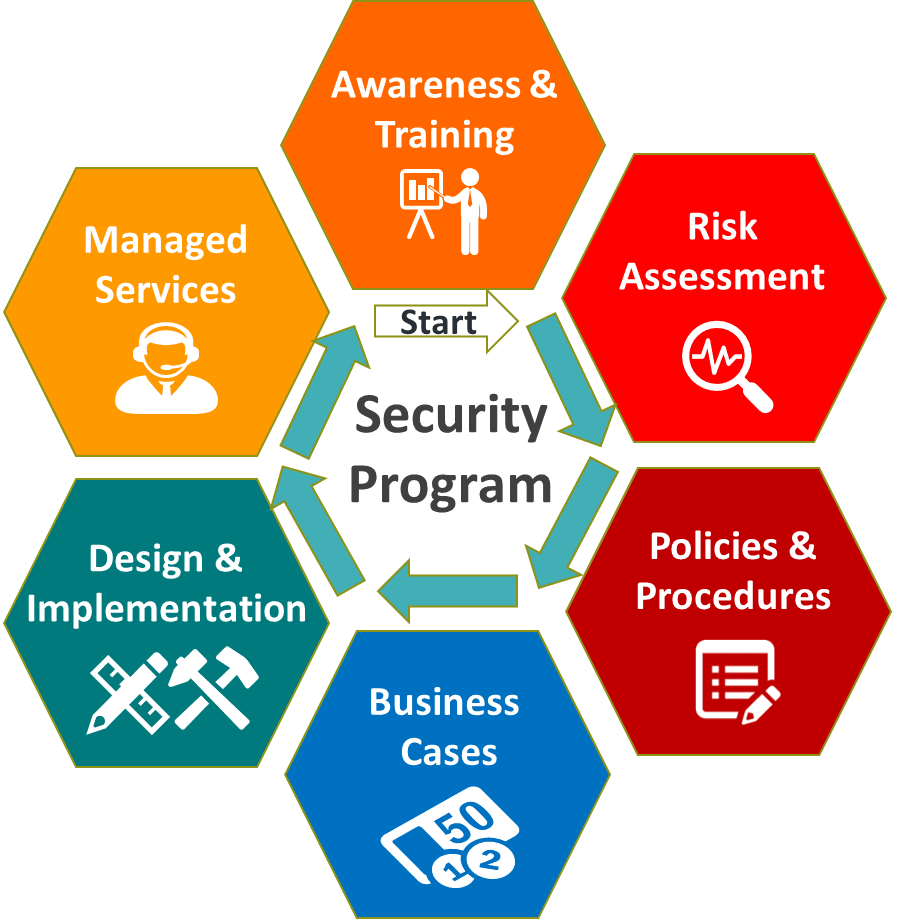
Yokogawa’s comprehensive security program life cycle covers the portfolio of security services which will support customer’s security journey to achieve the best working cyber risk management cycle. Please visit each webpage for detailed solutions and services.
The program offers a total of six phases pursuing Plan-Do-Check-Act cycle continuously.
- Awareness & Training
To keep educating and updating the employees about cybersecurity knowledge for correct decision making. Read more details - Risk Assessment
To identify exactly the existing security risks in a prioritized order based on system vulnerabilities and incident impact levels. Read more details - Policies & Procedures
To define the most practical policies and procedures for avoiding any gap between three main pillars-people, processes, and applied technology at the site. Read more details - Business Cases Development
To create the investment business case and build a security roadmap plan in mid to long term considering the budget and achievable goals. Read more details - Design & Implementation phase
To implement defense-in-depth information security countermeasures for keeping the operation availability at the highest level. Read more details - Managed Service phase
To implement enterprise-wide security managed services for timely monitoring, protection, and response at the first view. Read more details
Customer Benefits of Cybersecurity Lifecycle Management
Yokogawa’s Cybersecurity Lifecycle Management is a comprehensive security suite of indispensable solutions for the sustainability and efficiency of your control system.
- Security Program will align and improve the capabilities of the plant’s key elements-people, process, and technology to reduce the cybersecurity risk. It helps to overcome the great challenge of closing the gap between these three key elements.
- Taking individual plant’s lifecycle perspective, a developed security roadmap will support companies to create a mid to long term plan on how to carry on the security program lifecycle for their plant and in which manner to implement the countermeasures in achieving the company goals so that it is easy to understand the security journey by all the stakeholders.
- As a result, the security program brings more effective organizational team effort involving all employees. It greatly helps to strengthen employees’ higher commitment in their daily security performance as well.
- This program is run on a global methodology, executed in the same manner, following international security standards IEC 62443, a global standard for the security of Industrial Control Systems. Hence, no matter where the customer site across the world, the global Yokogawa team can reach out and deliver the same result.

Resources
Saudi Aramco's operations span the globe and the energy industry. The world leader in crude oil production, Saudi Aramco also owns and operates an extensive network of refining and distribution facilities, and is responsible for gas processing and transportation installations that fuel Saudi Arabia's industrial sector. An array of international subsidiaries and joint ventures deliver crude oil and refined products to customers worldwide.
- 16,000 FOUNDATION Fieldbus devices
- Main Automation Contractor (MAC)
- DCS anywhere concept integration with site SAP system
- Long term maintenance contract
- Sustainable development
Nitrogen Fertilizer Manufacturer Cyber Security Implementation Success Story
Discovering your Baseline with OT Security Risk Assessment
This white paper provides an overview of how Yokogawa believes its customers can best prepare for and position themselves to benefit from IIoT-enabled technology and solutions and digitalization in general to emerge as the successful connected industrial enterprises of the future.
yi-MAC stands for YOKOGAWA Innovative Main Automation Contractor:
- Full control of scope and schedule across packages
- Realization of customer expectation
- Single point of responsibility
- Providing fully integrated solutions
The ability to deliver a full scope of project execution capabilities is becoming more important than ever for automation suppliers that wish to compete on a global scale. Process automation suppliers have always had some degree of project execution capabilities, but only recently have suppliers and end users begun to realize the true economic impact that precise and comprehensive execution capabilities can have on the success of an automation project and on plant lifecycle costs.
The number of incidents involving attempted unauthorised access to computer systems via the internet as reported by CERT (Computer Emergency Response Team) was 137,539 in 2003. Statistics show an exponential increase in the number of reported incidents in the last five years. Although this can be partly explained by the increase in the number of computer systems in the world that are connected to the internet, it is nevertheless an alarming fact.
Yokogawa’s industrial automation (IA) product and service offerings, industry domain knowledge, and VigilantPlant approach – which emphasizes safe, secure, and uninterrupted operations -- provide a solid foundation for an Industrial Internet of Things that specifically addresses the requirements of process automation, particularly for the OT side of the equation. To be able to provide an equally solid foundation for the IT side, Yokogawa is partnering with Cisco Systems and other industry leaders.
Network and system security is now a necessity in process automation industry. YOKOGAWA provides a service lifecycle solution for cyber security to ensure that the security measures and deployments are continuously enhanced, monitored and inspected.
This white paper explains the details of the security design, implementation, operation and validation solutions from the technical perspective.
Initially when control and safety systems moved away from being hardwired and relay-based to computerized systems, vendors and asset owners were more interested in functionality than security. Typically, especially in high risk environments in refineries and off-shore oil installations, the systems were standalone with a dedicated Safety Instrumented System.
Over the last ten years more security solutions have available, and more industrial end users have implemented them to protect their businesses. Today nearly all companies use an anti-virus product installed on their industrial control system (ICS), as well as having their ICS segregated from the business network and the Internet by a firewall.
Harness the Future of Innovation
Highlights of the 2014 Yokogawa Users Conference and Exhibition
September 9 - 11, 2014, Houston, TX
By the editors of CONTROL Magazine
Downloads
Brochures
Videos
In our first episode, Tom Hardy debunks common false statements regarding Cybersecurity. Does insurance liability protect businesses against cyberattacks? Is my organization too small to be a target? Tune in to find out.
This workshop provided by industry partners Yokogawa and ThreatConnect will show you a way to strategically manage cyber risk within an industrial environment. Learn how to transition from the “break/fix” model of industrial cybersecurity to a business risk management strategy through cyber risk quantification, return on investment (ROI) for industrial cybersecurity solutions calculations, and cyber risk identification.
News
-
News Brief Sep 24, 2020 CISA Cyber Security Alert for Industrial Control Systems
The most recent alert released by the NSA and CISA has recommended immediate mitigations to increase the cyber defense posture of assets utilizing industrial control systems.
-
News Brief Sep 23, 2020 ICS Cybersecurity Solutions for Unsupported Operating Systems
A unique challenge facing operators of industrial networks is the limited ability to update the operating systems (OS) in servers and workstations. In many cases, the OS can be upgraded only during a plant shutdown. In today’s industry, plant wide shutdowns for a variety of maintenance activities and upgrade projects might not take place any more often than every 5-10 years.
Looking for more information on our people, technology and solutions?
Contact Us